
Password Security Risks: How Employees Risk Companies With Simple Codes?
- 05/05/2022
- Alex Smith
Updated on: 15/02/2023
794 Views | 0 Comments
The past two years have been pretty concerning owing to the increase in the password security risks and cybersecurity breaches, especially ransomware. The initial months of 2020 have seen a steady rise with the various ransomware attacks and have increased in the first half of 2021. By the end of the year 2021, 78.4 million attempted ransomware attacks had been recorded.
Considering the other hostage taking circumstances, the goal of the ransomware hackers or the malicious hackers is to steal the valuable data of the companies or gain access to their computer systems while demanding hefty sums of money before they abandon their hold on the hostage assets. That being said, at this point you might think that with all the latest security software developed and implemented in the companies, the ransomware gangs invest all their time developing the super sophisticated tools for attacking their victims.
In the following sections, we will explain that many of them actually modify their hacking techniques and begin attacking with the non-technical as well as peripheral invasion route which is none other than the human error. The development of the malware itself does never require any technical skills. However, the execution of this occurs as simple as when an employee clicks a file or link in a malicious email or SMS. It is crucial to remember that the ransomware attacks occur in various stages and it is mostly in the simpler phases that the full-blown attacks receive momentum.
A study conducted by the IT company, IBM, stated that the removal of human error from the equation would definitely lead to 95% of the prevented data breaches.
Table of Contents
- What Is The Issue With Highly Inviting Passwords & The Lenient Employees?
- How Bad Passwords/Simple Codes & Apathetic Employees Invited Biggest Cyber Espionage Attacks
- How Can The Employees Strengthen The Cybersecurity Of Their Company?
- What Are The Passwords Dos And Don’ts?
- The Most Common And Risky Passwords
- How Long Would It Take To Crack My Password?
- How To Check If Password Has Been Compromised?
- Final Words
What Is The Issue With Highly Inviting Passwords & The Lenient Employees?
Back in 2019, a research from the PreciseSecurity.com had identified the poor password security to be the third leading cause of the ransomware attacks, lack of employees’ cybersecurity training and phishing. Considering the three leading causes of ransomware infections, all of them actually originate from human errors or man-made errors.
In reality, the human brain is a very powerful organ that is highly capable of memorising multiple and lengthy passwords for different accounts especially if these are used regularly. However, in a survey conducted by Harris Poll and Google, 53% of people have been found to have the same password for multiple accounts while 13% used the same password for the entirety of their accounts. When combined together, the data suggests that 65% of people recycle their passwords even if they have the liberty to come up with new ones.
The survey had also suggested the trends in the contemporary cyber culture where the people seek for faster access and also a master access to their multiple devices and accounts. This is understandable that there is the monotony of regularly having to type the passwords or the reasonable difficulty in generating the strong passwords if we are considering the dozens of accounts.
However, this does not help the cause when 23.2 million data breach victims all over the world have been found to have used passwords such as “123456” while another 7.8 million has used passwords such as “12345678”. The worst part is that another 3.5 million in several countries chose to make use of the word “password” itself to offer them a barrier from the cyber thieves.
How Bad Passwords/Simple Codes & Apathetic Employees Invited Biggest Cyber Espionage Attacks
In this segment, we will see how poor passwords and apathetic employees have caused the biggest ransomware attacks through security vulnerabilities in history in just the past two years. This is just the period when people ought to possess even more knowledge and capabilities of defending themselves from the cyber criminals.
1. SolarWinds Cyber Espionage
The IT firm, SolarWinds, had been infiltrated by the suspected Russian hackers in the initial months of 2020. A trojan had been implanted into the updates of their monitoring software system known as Orion, that was in use by 33,000 of the high-profile customers of the company. This included thousands of the government employees here and abroad as well as the largest US corporations. The malicious code had then enabled the hackers to install even more malware that had permitted them to spy on the affected victims.
One of the security researchers has claimed to have warned the company under attack, SolarWinds, in 2019 that the password of the company for the update server is accessible to anyone. Apparently, the password was “solarwinds123”.
At a Congress hearing, the company had also argued that the weak password was an error made by their intern who has also shared the password on GitHub. Representative Katie Porter was so enraged by the revelation that she exclaimed,
“I’ve got a stronger password than ‘solarwinds123’ to stop my kids from watching too much YouTube on their iPad.”
To make the matter even more worse, the CEO of SolarWinds, Sudhakar Ramakrishna had admitted that the compromised password had been used since 2017. However, it was with 2019 warning by Kumar, that the firm had acted on it. Unfortunately, this was already too late.
The SolarWinds attacks is considered to be one of the biggest cyber espionage in history and is considered to have caused an average of $12 million financial loss per company that had been infiltrated.
2. The Colonial Pipe Ransomware Attack
Back in May 2021, the ransomware gang going by the name “DarkSide” had attacked the Colonial pipeline, which is a major diesel and gasoline pipeline system in the country and had caused the disruption of 50% of the fuel supply chain of the country.
The cyber criminals had already stolen nearly 100 GB of data from the company and had also made threats to make them public on the internet if the company refused to pay the ransom. For the fear of constant cyber attacks, The Colonial Pipeline had decided to shut down their operations and also paid $5 million as ransom to DarkSide. The ransomware attack had affected the fuel supplies in the airports and hampered the flight schedule and also caused panic buying.
CEO Joseph Blount, at a Senate hearing had revealed that the attack was initiated by an employee when he logged on through a legacy Virtual Private Network (VPN) that was solely set up by the single factor authentication. This meant that the secondary passes like the security codes that usually are sent to the registered mobile phones were not at all necessary to access it.
The cybersecurity firm that was consulted in the bid to analyse the attack, theorised that the employee might have already used the same password on an earlier compromised website.
3. The New Cooperative Ransomware Attack
Just nearly an year ago, the Iowa-based farming cooperative named NEW Cooperative had been attacked by a Russian ransomware gang going by the name BlackMatter, which had been believed to be the rebranded version of DarkSide. The cybercriminals had demanded $5.9 million payment in the bid to restore the access to the computer systems of the coop that they had used for feeding 11 million animals that included chickens, cattle and pigs.
The Chief Operating Officer of digital identity security company FYEO, Tammy Kahn had analysed that the ransomware attack on the company had been possible by the use of the bad passwords by several employees.
When FYEO had audited the company or the website of NEW Cooperative on their database, they had discovered that the organisation possessed 653 passwords that had been compromised in the past. For making the matter most worst, it had been discovered that the most common password used among the 120 employees was a combination of an all-too-common animal of the farm and the number that comes very first when counting - “chicken1”.
This is such a simple password that is bound to fail, keeping aside the brute force hacking tools and the phishing campaigns. The email addresses of the employees and the executives had been shared online publicly. In such a situation, all the hackers have to do is simply guess the passwords by matching the niche, numbers, anything related to the company or business and something like “chicken1” is a dedicated giveaway.
How Can The Employees Strengthen The Cybersecurity Of Their Company?
The companies at this point of time must invest in the fundamental cybersecurity practices. The difference in settling for a repetitive as well as let alone highly-simplistic password in addition to taking time to come up with the stronger ones can serve to be the protection of hundreds and thousands of the financial assets of the company. As a matter of fact, a white paper by the cyber insurance firm named Coalition had stated that the average ransom that the cyber criminals had demanded rose from $230,000 in the first quarter of 2020 to a whopping $337,669 in just the second quarter of the same year. This is steeply a 47% increase in just 6 months!
The businesses and the other organisations must also take note that the cyber criminals usually conduct allied operations with the other related gangs. Thus, as soon as the passwords get compromised, there is a far better chance of the acquired passwords to get rapidly shared in the underground forums and thus increasing the points of the attacks. A research by Agari has discovered that the compromised passwords are quickly feasted upon as soon as they are shared in the forums and the phishing websites. When they had posted the credentials of the fake accounts on these portals, 20% of them had been infiltrated in just an hour while 40% of them had been breached within the next six hours.
The following are some of the practical tips to avoid password security risks that even the employees with no computer science background can implement for strengthening the cyber defences of their respective companies.
✅ Be Creative With Your Passwords
As with the cases of SolarWinds and NEW Cooperative, the sophisticated cyber attacks can occur even with the minute dents in the cyber wall. So, how would you come up with something practical other than solarwinds123 and chicken1?
The very first thing to check is the password requirement of the account. In the current time, most of the platforms need the users to include a lowercase letter, an uppercase letter, a symbol and a number.
The character substitution and the passphrases are great combined strategies to create a password from the ordinary words. For instance, you have a pet named Cookie and you can choose a passphrase like: The cookie is sweet. Then you can substitute some of the alphabets with symbols and numbers such as replacing “o” with 0 or @, “i” with 1 and “s” with 5 or “e” with €. Thus, your passphrase becomes: Th€ c0@k1€ 15 5w€€t. It might be awkward at the very first to type. However, your brain will adapt quickly with the multiple repetitions.
The best part with the passphrases + character substitution is that they treat the propensity of the human brain to retain things that are personal or meaningful, not as any hindrance but as an advantage. You can additionally combine words from things that are close to you such as your family members, places. But you have to keep in mind to string them into phrases and not just merely keep the words and come up with unique codes.
The passphrases are definitely easier to retain in mind as compared to a random jumble of characters. And the character substitution with codes can be repeated into other passwords and that it is solely you who knows what the code stands for.
✅ Include Foreign Words
If you know how to speak any foreign language, then you must consider using your linguistic skills for strengthening your passwords. The internet communication as well as the transactions are usually in the English language and thus, if you can come up with a password like “Les@coupes gl@cées-5ont-p0ur le 1dim@nche” (Les coupes glacées sont-pour le dimanche”) which means “Sundaes are for Sundays” where some alphabets have been transformed to @ while adding some hyphens and that the hackers would have a hard time finding it.
If the passwords have been generated in English, the hackers would have more chances of cracking it as it sounds like a common phrase. The hackers would have a hard time cracking it even if they possess brute force hacking software which is most likely set in English. Another good thing with the use of the foreign words is that they keep your brain healthy as it becomes a cognitive exercise. Thus, it brings in a nice motivation to learn any other language.
✅ Use A Reputed Password Manager
Going back to the survey of Harris Poll and Google, it was sad to find out that only 24% of the respondents made use of the password manager and solely 55% was able to define the term correctly. Therefore, this must prompt teh companies to implement the systems where their employees must use and gain more education regarding the benefits of the password managers.
For all of those who would like to avoid the burden of having to remember and type the lengthy and randomised passwords for different accounts, the password managers are a great solution owing to their sync and the password generating abilities permit the ease of access to the various accounts and keeping weak password security risk at bay. That being said the password managers need to be reputed one and you need to do proper research to find out if your data can be breached through password manager as password managers security risks are quite common for the unknown ones.
One infamous hacker had turned to a security consultant who stated:
“A password manager allows you to manage the rest of your credentials, so you choose a master password to unlock the password manager, and the password manager takes care of the rest. And you could actually configure these password managers to randomly create, for example, 15-character passwords.”
What Are The Passwords Dos And Don’ts?
The passwords dos and don’ts are not only meant for desktops and laptops but also covers solutions to eradicate password security risks iPhone. Some of the other best practices in the form of dos and don'ts to keep away password security risks include the following:
✅ The passwords must be a minimum of 8 characters in length. Ideally, if the system permits, you must definitely choose passwords with 24-26 characters long.
✅ Never create passwords with the missing or repeated letters, keyboard patterns and common phrases. You must remember that the malicious hackers never guess your passwords. Rather they employ password cracking tools that possess the capability to bypass all those simple tricks and can crack the passwords in just a matter of seconds.
✅ Avoid the following in your passwords:
❌ Address (home and office)
❌ Date of birth
❌ Personal, child or spouse birthday
❌ Phone number
❌ Anything about you posted on various social media sites as an interest, including sports teams, hobbies, cars, etc.
✅ Avoid using some common terms such as:
❌ Admin
❌ Baseball
❌ Batman
❌ Football
❌ ILoveYou
❌ Princess
❌ Qwerty (in any form without special characters)
❌ Sunshine
❌ Superman
❌ Welcome
❌ Sports teams, like Liverpool or Manchester in the United Kingdom or Cowboys or Lakers in the United States
❌ Swear words – very common, actually. The “f” word ends up getting turned back on you when the hacker is attempting to break into your account, though.
✅ You must use different passwords for different accounts and also avoid recycling your account passwords. Make sure to change the passwords frequently.
✅ You must create answers for the web security questions that are pretty hard to answer but at the same time easy to remember for you.
✅ Never share your passwords with others. This one might seem to be obvious, however, this happens way too often. Sharing is definitely a good thing but not at all when it comes to security and passwords.
✅ Never write down your passwords and hide them. If it is essential to write them down for whatever reason, you must not label them as “passwords”. You must write down something else that you will only understand.
✅ You must refrain from storing your passwords on the websites, your computer or even in the web browsers unless they are strongly encrypted software program. In case of your device getting hacked or stolen, the stored passwords will offer easy access to any of the would-be hackers.
✅ Make sure to use passwords whenever and wherever required. You must secure anything that you can actually secure with a password.
The Most Common And Risky Passwords
Just for your knowledge of some most common and risky passwords, here is a set of examples that you must never use. This password list has been offered by the most common passwords in the United States, under the courtesy of the National Cyber Security Centre’s global breach analysis. You can show this to your employees as an example and ask them to not use them anywhere. Also, if you possess any of these weak password examples, you must change it immediately:
- 123456
- 123456789
- Qwerty
- Password
- 111111
- 12345678
- Abc123
- 1234567
- Password1
- 12345
How Long Would It Take To Crack My Password?
The passwords such as qwerty, password and 123456 and the most common in them the “password” that appears on the list of the most common passwords and must definitely be retired from the use. As revealed in the data by the website Security.org, adding even one of the uppercase letters to a password can instantly dramatically alter its potential. In the instance of the 8 character password, it can now be cracked in 22 minutes instead of the instant in one second or less, an increase of over 1000 percent.
While the added time in such a case is definitely not good enough to end up with a satisfactory password, the high security gains of making use of the characters other than the lower case letters can be multiplied. When using at least one upper case letter and a number, an 8 character password will now take a computer 1 hour to crack. With another symbol added to the password, it takes another 8 minutes. A 12 character password having one uppercase letter, one symbol and one number is almost unbreakable, which takes a computer 34,000 years to crack.
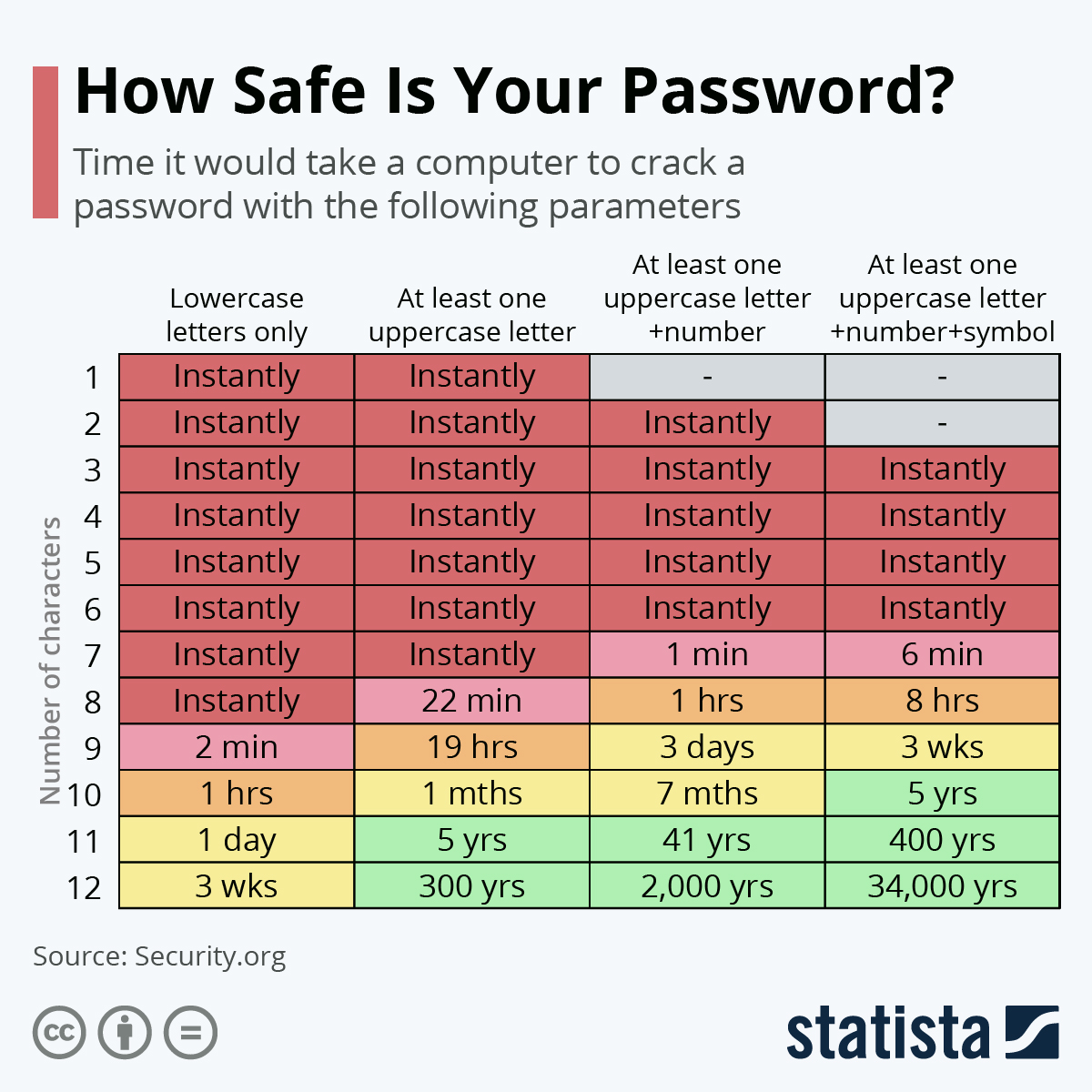
This usually happens as when we use more kinds of characters, the potential combinations making up the password increase exponentially. With solely the 26 lower case letters, a password containing 8 characters possesses 26^8. This will fetch around 209 billion possible combinations. As you add the uppercase letters, we already arrive at 52^8, which offers around 53.5 trillion combinations. With the added numbers, it is 62^8 or 218 trillion combinations.
Additionally, the symbols offer another great potential for security. Since, only a handful displayed on the computer keyboards are convenient to use. This raises the combinations once more to around 90^8 offering 430 trillion combinations.
How To Check If Password Has Been Compromised?
You might have searched for queries like “how to check if i have been hacked” and you have been returned with a lot of results. Probably you have not found the correct site with authentic information. So, how would you check if your password has been compromised by the hackers? The simple answer to this is HaveIBeenPwned.
Basically, the term “Pwned” comes from the origin in the video game culture and is a leetspeak derivation of the term “owned”. The website is a tracking tool that checks for compromised passwords against data breaches. The website has been created by an Australian web security consultant Troy Hunt where the website analyses information from hundreds and thousands of data breaches and compromised accounts, often whose credentials are traded in the various black markets and dark forums.
The online free tool HaveIBeenPwned lets the users search for their information, sign up for notifications (email), and prevent other people from seeing your data. All you have to do is just feed the search engine of the website with your Email ID or your mobile number. As soon as you press the “Pwned?” button next to the search engine, in a couple of seconds, you will be displayed if your email Id or your phone number has been hacked. It also offers you details such as which websites that you have used got hacked and what to do next.
Final Words
Password security risks exist when you are not aware of the small mistakes you have been making till now. With the password related threats prevalent with the account, it does not mean that you will not be using the passwords. Passwords must be used when and where possible. But you have to be very proper with the rules of keeping the passwords. Additionally, password risk assessment is vital for the companies since social engineering attack on a password can prove to be disastrous financially for the companies.
