An intruder considers a limited time frame to look for the loopholes and vulnerabilities in the information system’s security that lacks priority. Unfortunately, minor vulnerabilities may wind up in critical consequences paving the way to compromised systems. The proven way to reduce such risks is by employing penetration testing.

CVE details state that over 13% of the vulnerabilities bear a critical score (CVSS) of 9.0 to 10.0, while the remaining 77% have a score of 1.0 to 8.0.
Thus, it is crucial to know when you must undergo pentesting. Here is when:
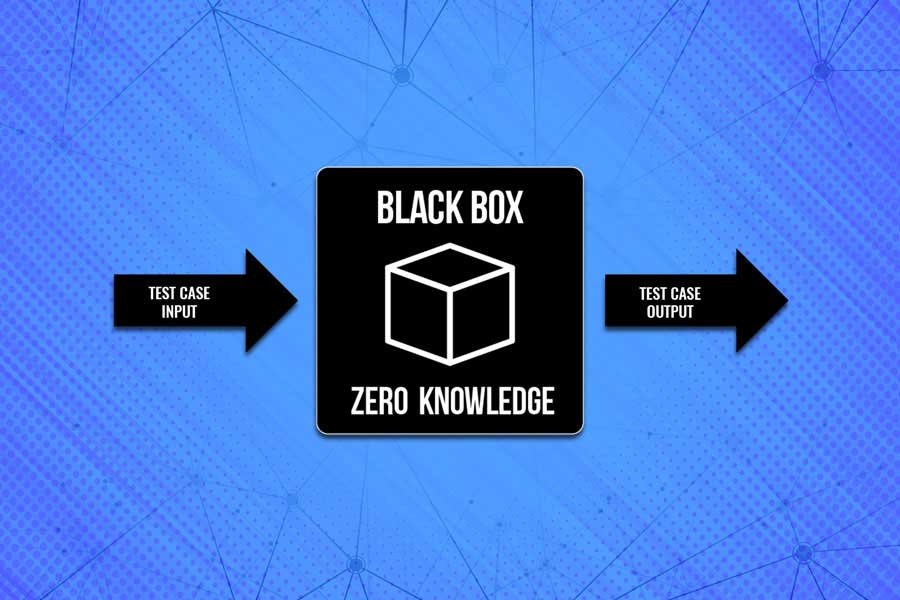
We work in a real-life environment possessing strictly limited knowledge of your network and zero information on the usage of network structure, security policies, software and network protection.
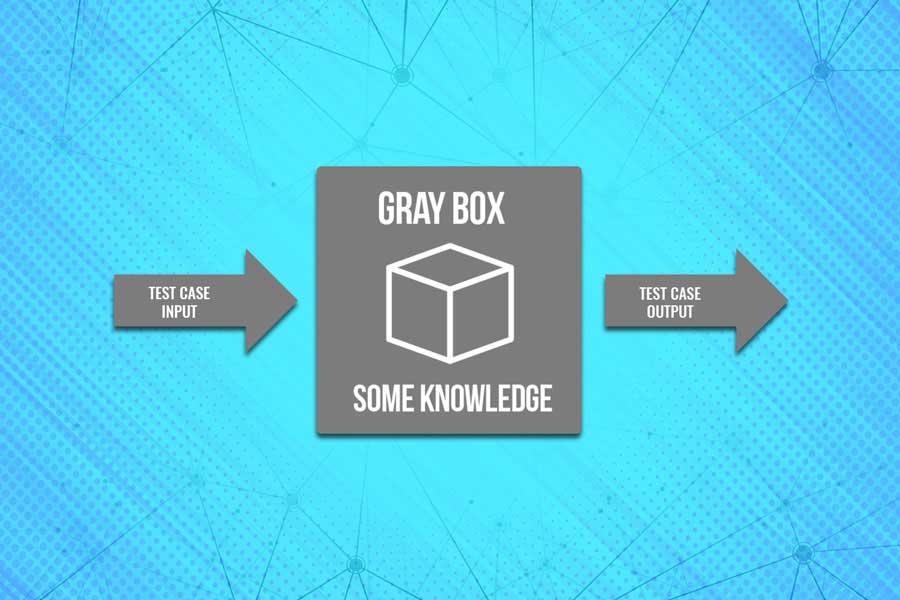
We carefully examine your system with information on your network like architecture diagrams, the network’s overview or the user login details.
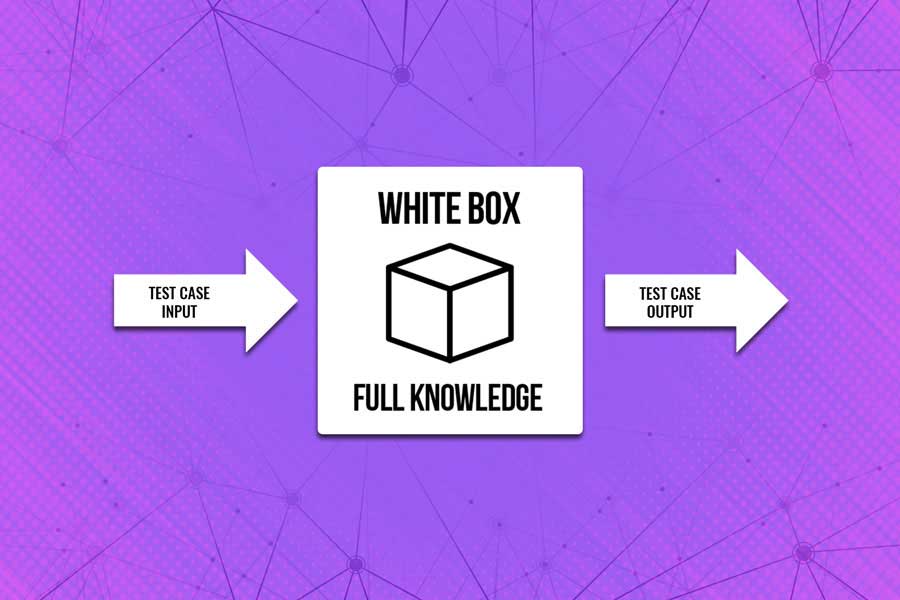
We spot the potential weakness points utilizing the admin rights and the access to the server configuration files, source code or architecture documentation and database encryption principles.
At the end of our pentesting process, we furnish our customers with an extensive set of reports inclusive of recommendations for effectively eliminating the detected data breaches:
A pen test isn't a one-time test. The network servers and computers function as an entire system to guard your brand reputation in order that you ought to be ready to safeguard the info of your clients and customers. This is often major thanks to promoting corporate reputation also. At Pattern Drive Private Limited we assist you with the factors which will decide the frequency of penetration testing services for your organization: